
KeePass exploit will help retrieve cleartext grasp password, repair coming shortly
Table of Contents

The popular KeePass password manager is vulnerable to extracting the master password from the application’s memory, letting attackers who compromise a gadget to retrieve the password even with the database is locked.
The challenge was found out by a safety researcher recognised as ‘vdohney,’ who posted a proof-of-strategy device allowing attackers to extract the KeePass grasp password from memory as a proof-of-principle (PoC).
Password managers let customers to make distinctive passwords for just about every on the internet account and keep the credentials in an simple-to-search database, or password vault, so you do not have to remember each individual 1. Even so, to correctly secure this password vault, buyers ought to bear in mind the one particular grasp password made use of to unlock it and entry stored qualifications.
This learn password encrypts the KeePass password databases, blocking it from becoming opened or read without first getting into the password. Nonetheless, once that learn password is compromised, a menace actor can access all the credentials stored in the database.
Therefore, for a password supervisor to be effectively secured, it is critical that consumers guard the grasp password and not share it with everyone else.
A new KeePass vulnerability tracked as CVE-2023-3278 makes it doable to get well the KeePass grasp password, apart from the initially one particular or two characters, in cleartext form, irrespective of irrespective of whether the KeePass workspace is locked, or potentially, even if the software is shut.
“KeePass Master Password Dumper is a straightforward evidence-of-notion software utilized to dump the grasp password from KeePass’s memory. Aside from the 1st password character, it is mostly ready to recuperate the password in plaintext,” warns the protection researcher on the GitHub site for the exploit device.
“No code execution on the target process is necessary, just a memory dump. It does not make a difference where the memory arrives from – can be the procedure dump, swap file (pagefile.sys), hibernation file (hiberfil.sys) or RAM dump of the entire system. It isn’t going to matter whether or not or not the workspace is locked.”
The flaw exists due to the fact the computer software works by using a custom made password entry box named “SecureTextBoxEx,” which leaves traces of every single character the consumer sorts in the memory.
“KeePass 2.X employs a custom-made textual content box for password entry, SecureTextBoxEx. This textual content box is not only utilised for the learn password entry, but in other sites in KeePass as perfectly, like password edit boxes (so the attack can also be made use of to recover their contents),” points out vdohney.
The vulnerability impacts the hottest model of KeePass, 2.53.1, and as the plan is open-source, any project forks are probable impacted.
KeePass 1.X, KeePassXC, and Strongbox do not seem to be impacted by CVE-2023-32784, in accordance to the developer of the password dumping tool.
Also, while the PoC was analyzed on Home windows, the exploit need to also get the job done for Linux and macOS, with some modifications, as the issue is not particular to the OS but how KeePass handles person input.

Source: vdohney
Effortless to exploit
Because memory dumps ought to be retrieved for the KeePass grasp password to be recovered, the exploitation of CVE-2023-32784 requires actual physical obtain or malware an infection on the concentrate on device.
However, data-stealing malware could speedily check if KeePass exists on a personal computer or is functioning, and if so, dump the program’s memory and send it and the KeePass database back again to the attacker for offline retrieval of the cleartext password from the memory dump.
BleepingComputer tested vdohney’s ‘keepass-password-dumper’ device by setting up KeePass on a exam system and producing a new database with the master password ‘password123,’ as revealed down below.
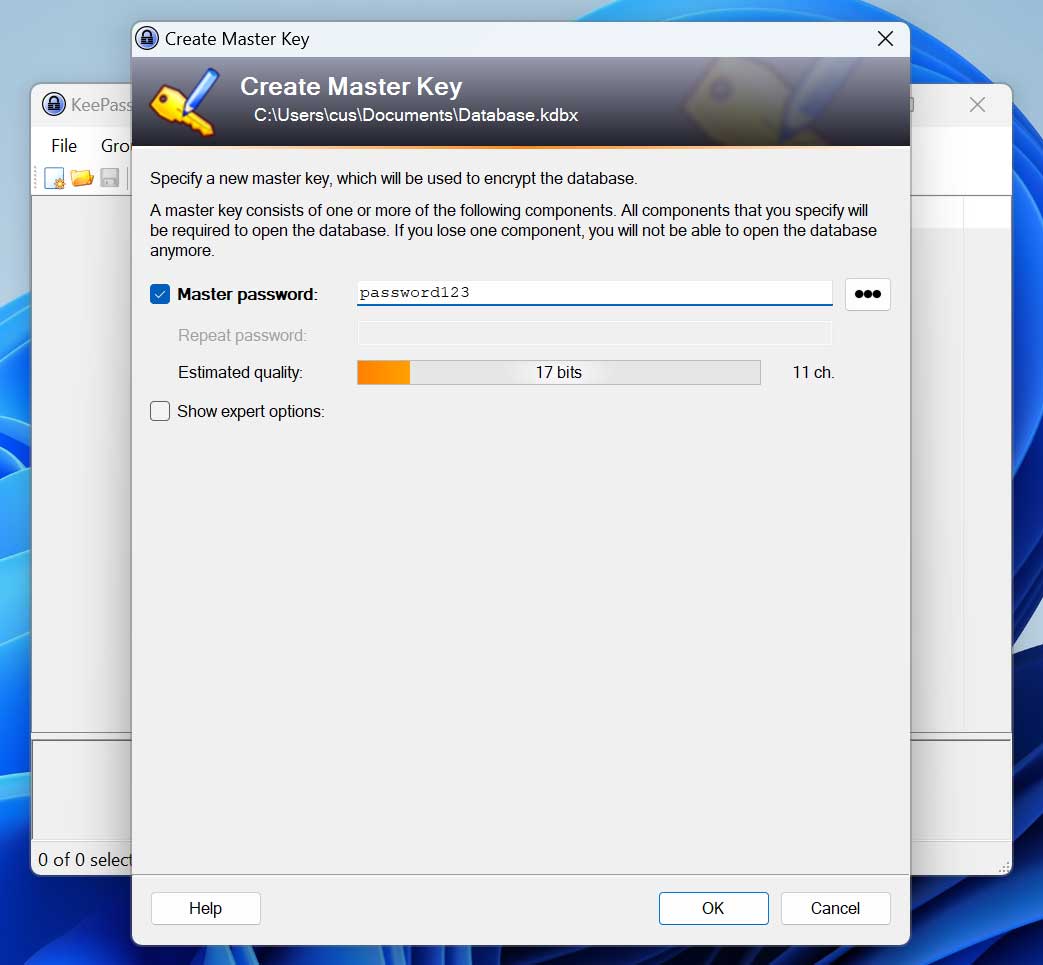
Source: BleepingComputer
We then locked our KeePass workspace, which prevents obtain to it unless you enter the master password again.
In our tests, you can use Process Explorer to dump the memory of the KeePass undertaking, but it needs a full memory dump, and not a minidump, to do the job correctly. No elevated privileges are wanted to dump the processes’ memory.
Immediately after compiling vdohney’s instrument utilizing Visible Studio, we executed it versus our memory dump, and it quickly recovered most of our cleartext password, with just the to start with two letters lacking.
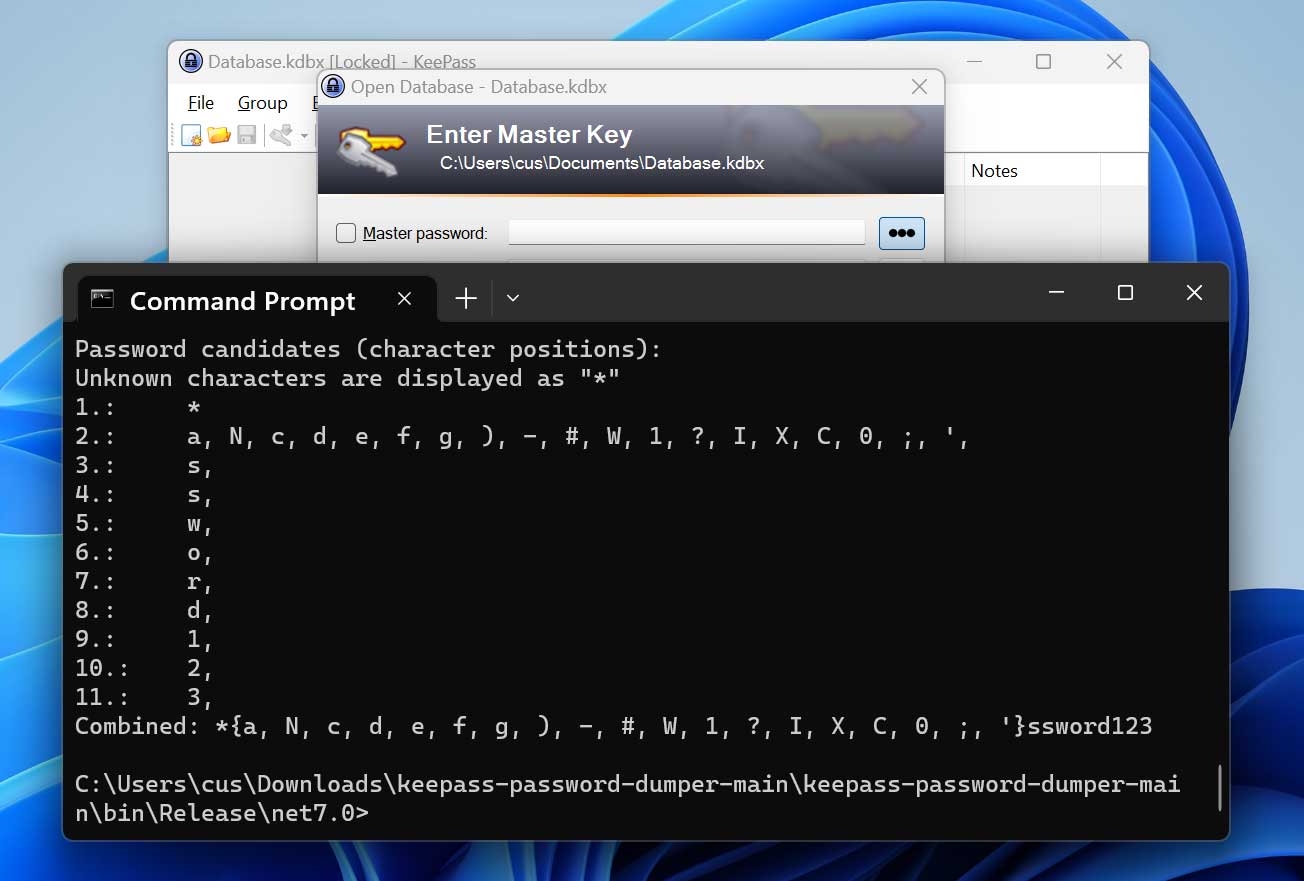
Supply: BleepingComputer
Though this is not the full password, determining what characters are lacking would be relatively straightforward.
The researcher also warns that learn passwords made use of in the past can continue being in memory, so they can be retrieved even if KeePass is no more time functioning on the breached laptop.
Take care of coming shortly
The developer of KeePass, Dominik Reichl, gained the bug report and promised to roll out a deal with for CVE-2023-32784 on model 2.54, anticipated someday in July 2023.
However, Reichl advised BleepingComputer that KeePass model 2.54 is far more very likely to be released to consumers in about two weeks, so it really should be out by early June.
Dependent on a dialogue where Reichl created his thoughts on the stability flaw and the prospective mitigation strategies, two protection enhancements are described for the future KeePass variation:
- Accomplish direct API calls for having/location the textual content of the textual content box, averting the development of managed strings in memory that can leak secrets.
- Produce dummy fragments that contains random characters in the process memory that will have somewhere around the same size as the user’s learn password, obfuscating the serious key.
KeePass 2.54 for Home windows will have both of those, although macOS and Linux variations will only get the next enhancement.
The developer has launched a examination edition with the new safety enhancements that mitigate the difficulty, so those who can take unstable conduct can supply it from listed here.
The creator of the PoC has confirmed that he can no lengthier reproduce the assault with the two protection enhancements in place, so the deal with seems to be effective.
Even just after the new variation is launched, the grasp password may well however be saved in memory documents. The researcher warns that to be 100% risk-free that it is not lurking on the program, you would need to delete your system’s swap and hibernation documents, format your really hard push applying the “overwrite information” manner to avoid info recovery, and do a new OS install.
For most, nevertheless, restarting the laptop, clearing your swap file and hibernation information, and not working with KeePass till the new edition is introduced are sensible basic safety steps for the time being.
Even then, for the very best safety, be tremendous vigilant about not downloading systems from untrusted internet sites and beware of phishing attacks that may infect your gadgets, giving threat actors distant accessibility to your product and your KeePass databases.
